Block Chain Security: How Social Engineering Threatens Cryptographic Security
Blockchain a P2P (Peer to Peer), technology for payments and settlements, is a cryptographically secure means of storing and proofing assets, however that does not mean it is not fallible from human caused error.
Tartoshi
12/1/20258 min read
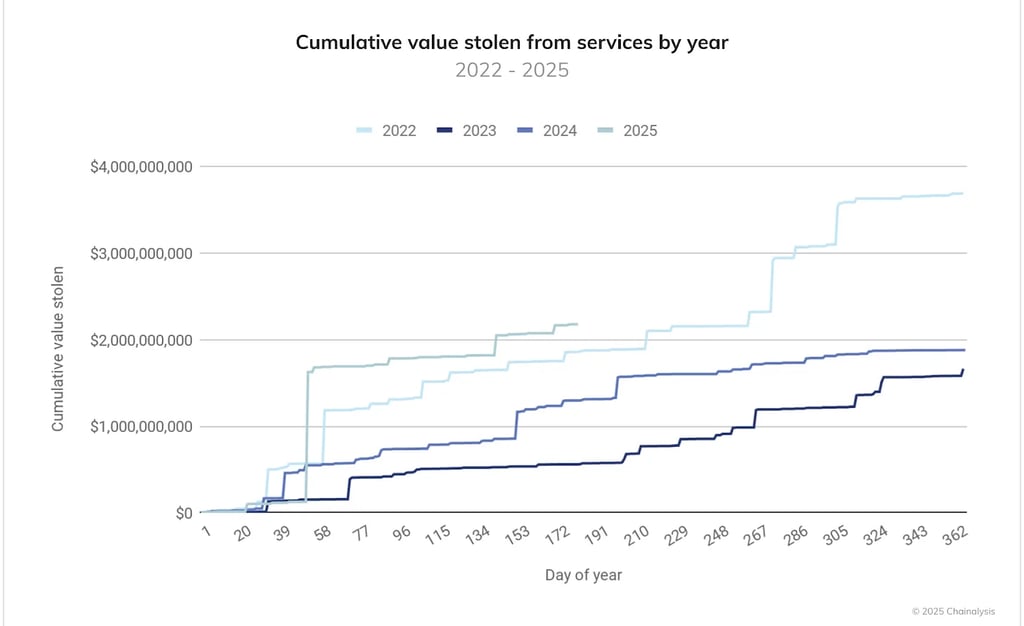
Blockchain a P2P (Peer to Peer), technology for payments and settlements, is a cryptographically secure means of storing and proofing assets, however that does not mean it is not fallible from human caused error. According to chainalysis Cryptocurrency hacks have accounted for over $2.17B in stolen customer assets so far1 this year. This number is no anomaly, in fact on average $3-4B has been consistently stolen from users every year on average according to the 2022-2025 data. One of the largest crypto hacks in history occurred early, in Febuarary this year, the Bybit hack totaling ~$1.4B in user funds. With so much on the line, it is important for users and exchanges to be vigilant in protecting their assets.
Blockchain assets are user-controlled sovereign assets that are safely protected behind a private key. A private key is mathematically linked to a public address and serves as the sole credential proving ownership of the funds held within it. Anyone with access to your private key, has complete access to your wallet, and your funds. Making it both a powerful tool and a significant point of human error and failure. Unlike traditional banking, there is no customer support line to recover a lost password or reverse an unauthorized withdrawal. Once you lose access to your keys, you lose access to your crypto. Now having control over your funds and private keys, has many of its own benefits, one being completely censorship resistant. Imagine for example you are a citizen in a country without protections of political speech, and you make an unpopular remark one day, and the next day you come to find out the government has frozen access to your bank accounts and seized your assets. Bitcoin and other blockchain assets make this type of tyranny impossible, and that’s why many people across the world choose it. Many others choose it for this censorship resistant property alongside its fixed supply, making it resistant to the debasement of currencies. However, the downsides come into play when stores of value such as Bitcoin or other Blockchain currencies become points of vulnerability for their users, as they were in the Bybit attack for example. We will talk in depth about this exploitation, and the failure points as we go on in this essay, but first let’s talk a bit more about the architecture of bitcoin and its security vulnerabilities alongside the vulnerabilities of other blockchain forks of bitcoin.
Bitcoin is inherently infallible in its code, it is clear and immutable, transactions are confirmed through a decentralized network of nodes, who then solve secure SHA-256 hashes and settle transactions in blocks, which then improve its total security. The only two known ways of disrupting its architecture is through quantum decryption, or a 51% attack. In a 51% attack, a group of rogue miners must acquire 51%+ of the total hash power or computing power of the network2. In which they can then go in and change consensus for the entire history or ledger of transactions. They can rewrite funds from one address to another, taking control of funds from Satoshi Nakamoto’s wallet for example. A rogue actor requiring 51% of all hash power in one forceful takeover, would require a global infrastructure of computing worth multiple billions of dollars and electricity resources that would raise flags for any national grid, making it highly improbable for a criminal group to engage in this sort of activity.
In quantum decryption, the cryptographic hashes that secure the bitcoin network can be engineered to go from uncrackable to breakable by using quantum supercomputing to solve the hashes that would otherwise take 10^65 years to brute force with the most powerful computers today3, for context the universe is only 1.38 x 10^10 years old. Quantum computing breaks the Elliptic Curve, that safeguards the user’s private key, to automatically in theory derive the private key by just knowing the public wallet address of the user. Quantum computing resistance is an area of research that has been well developed, and there are many methods of preventing quantum decryption, many of methods which have already been implemented into alternative blockchains. This area of research is known as Post-quantum cryptography, and the NIST (National Institute of Standards and Technologies) has already released four cryptographic resistant algorithms4 . Implementing such a standard to bitcoin is very much possible, as there is a decentralized voting process known as a Bitcoin Improvement Proposal, or a BIP to upgrade the network5 and there have been many examples in the past of miners and users accepting and implementing these improvement proposals. So my strong belief is that the bitcoin stakeholders would be quick to implement and fork such a solution, with ongoing proposals constantly being discussed and nearly $2T of value at stake.
The largest cryptocurrency theft ever on record, occurred just earlier this year. The Bybit $1.4B dollar hack, where over 400,000 ethereum were taken out of a gnosis safe and transferred to the North Korean State Sponsored group Lazarus. Lazarus has been infamous for hacking the likes of Sony Pictures in 2014, leaking sensitive employee and customer data, and destroying nearly 70% of Sony laptops and computers6 . Lazarus group additionally has been tied to over $3.4B in aggregate crypto theft since its inception in 20076 . Including attacks on other major blockchain exchanges and protocols such as BingX, Poloniex and Phemex7 .
A gnosis safe wallet, is a secure means of including multiple signers to approve a cryptocurrency transaction. Where there are a number of parties who must sign off on a transaction, before it can be approved. The gnosis safe, is a hardcoded smart contract that is directly within the architecture of the funds at the exchange protocol. In Bybit’s case there were three signers, who had to approve a transaction for the exchange’s vaulted funds. The gnosis safe in itself has been a consensus method of providing an additional measure of safety for blockchain currencies, however its implementation is again not infallible. While the multi-signature requirement provides strong cryptographic security, it fails to account for human error and vulnerabilities in the user interface layer. The Bybit hack exploited this exact weakness not by breaking the cryptography or compromising the blockchain itself, but by manipulating what the signers saw when they approved transactions.
The Lazarus Group executed this theft through a sophisticated two-phase attack. First, they compromised a developer’s machine at Safe{Wallet} formerly Gnosis Safe, the third-party service Bybit used to manage their multi-signature wallet. Through this access, attackers injected malicious JavaScript code into Safe{Wallet}’s web interface that specifically targeted Bybit’s wallet addresses and authorized signers8. When Bybit’s three signers logged in to approve what appeared to be a routine internal transfer on their screens, the malicious code secretly intercepted and modified the transaction data before it reached their wallets for signing. The signers’ hardware wallets displayed slightly different data including a critical change from a normal “call” operation to a “delegatecall” operation but the non-human-readable format of the EIP-712 signature made this nearly impossible to detect8. After the signers approved what they believed was a legitimate transaction, the JavaScript replaced the signed transaction data back to the original format before sharing it with other signers, allowing the hackers to start their attack vector. Once all three signatures were collected, the attacker submitted the transaction on-chain, which executed a delegatecall to a malicious contract disguised as an ERC-20 token transfer. This delegatecall modified a storage slot of Bybit’s proxy wallet contract, changing the implementation address from the legitimate Gnosis Safe contract to an attacker-controlled contract8. With this single transaction, Lazarus gained complete control over Bybit’s cold wallet, allowing them to drain all $1.4 billion in assets and begin laundering the funds across multiple blockchains and exchanges. The breadcrumbs tying this attack to the Lazarus group, is publicly available using blockchain forensics7.
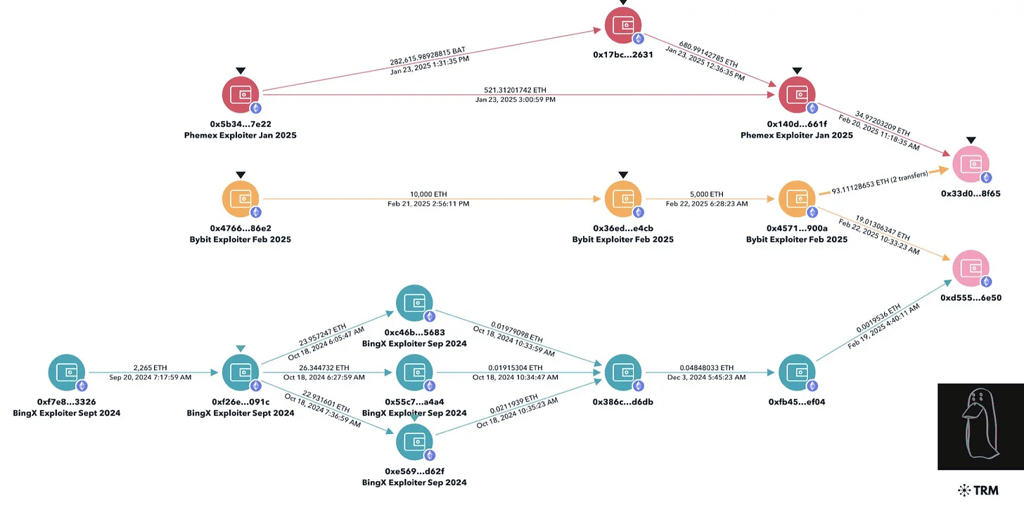
ZachXBT Identified On-Chain Addresses Linking the Phemex and BingX exploiters to the Bybit Exploiter
There is a famous saying that has been echo’ing the humdrums of crypto for many years. “Not your Keys, Not your Crypto.” Which means if you don’t personally have sovereignty over the private keys of your crypto, you don’t necessarily have full control of your coins. This ethos is mostly correct, the cypherpunk movement, the original bitcoiners were right to want to shield their coins from potential tyranny of governments, centralized exchanges, and centralized financial institutions. We have seen time and time again, throughout history centralized power has the ability to cause harm to the everyday person if abused. Whether that means, a financial recession rendering your funds insolvent at a regional banking branch which has happened in the 08’ financial recession and more recently in the Silicon Valley Bank collapse. Or when a cryptocurrency exchange goes insolvent due to mishandled customer funds, such as the example of the FTX and Celsius collapse in 22.’ Or say if you are a nation state and your access to the global banking system is sanctioned, and your funds are frozen, for example that of which happened with Russia and its revocation from the SWIFT banking system in 23’. There are many incentives to want to have private control over your private keys. Whether these are immoral systems or not, is not the topic of this essay. This is in essence why blockchain currencies were created.
However, I think it is incredibly important to want to safeguard your assets with proven methods of security. Firstly, as we have seen with the Bybit hack, cryptocurrency exchanges might not be the safest place to store your funds. So let’s talk about cold storage. Cold storage refers to keeping your private keys completely offline, isolated from any internet-connected device that could be compromised by malware, phishing attacks, or remote exploits. The most secure and user-friendly form of cold storage for the average person is a hardware wallet, a physical device specifically designed to generate and store private keys in a secure piece of hardware that never exposes them to your computer or the internet. Hardware wallets such as Ledger and Trezor function as dedicated cryptographic devices that sign transactions internally without ever revealing your private key to external systems.
We know that today, 98% of all successful cyber attacks don’t start with super sophisticated malware or advanced scripting methods (although in the end they may be exploited that way), but instead start with simple Phishing attempts as an attack entrance. Even with the Bybit hack, although the hackers didn’t initially find a vulnerability within the smart contract, they were able to inject javascript code into what that forensics showed started with a compromised computer of a safe{wallet} developer8. This attack started with a compromised employee computer, through a phishing attempt, that then compromised the UI state of the safe. Similarly we know that many cryptocurrency thefts start with phishing attempts, emails disguised as those from Coinbase customer service, texts from Genesis stating your “funds may be at risk,” and spam calls from bad actors posing as exchange employees. Although your blockchain currencies may be cryptographically secure, and you may have full control of your keys, basic human error can still lead you into revealing your private key accidentally to these cunning bad actors. It is very important you stay diligent, and keep your private keys secure in a safe that is well custodied, or with an institutional custodian.
There are today many institutional custody solutions that provide professional grade security for cryptocurrency assets, including firms like Coinbase Custody, and Fidelity Digital Assets. These custodians employ multi layered security protocols including geographically distributed cold storage, insurance policies, and teams of security professionals. For the average everyday investor this reality is simple and safer. Most users are likely better off holding Bitcoin through regulated exchange-traded funds (ETFs) such as BlackRock’s iShares Bitcoin Trust (IBIT). When you hold IBIT shares in a traditional brokerage account, you gain exposure to Bitcoin’s price movements without taking on the operational security risks of self custody. BlackRock handles all custody arrangements through Coinbase Custody, and your investment is protected by the same securities regulations that govern traditional financial assets. The advantages are substantial, and there is no risk of losing private keys, no vulnerability to phishing attacks, no concerns about hardware wallet failures, and no exposure to exchange hacks like the Bybit incident.
[1]https://www.chainalysis.com/blog/2025-crypto-crime-mid-year-update/
[2]https://www.coinbase.com/learn/crypto-glossary/what-is-a-51-percent-attack-and-what-are-the-risks
[3]https://bitcoinvn.io/news/how-hard-crack-private-key/
[4]https://csrc.nist.gov/projects/post-quantum-cryptography
[5]https://www.theblock.co/learn/271532/what-is-a-bitcoin-improvement-proposal-bip
[6]https://www.csis.org/analysis/bybit-heist-and-future-us-crypto-regulation
[7]https://x.com/zachxbt/status/1893211577836302365?lang=en
[8]https://www.nccgroup.com/research-blog/in-depth-technical-analysis-of-the-bybit-hack/
